
Cybersecurity researchers have discovered multiple campaigns targeting Docker Hub that have planted millions of malicious “imageless” containers over the past five years, once again highlighting how open source registries pave the way for supply chain attacks.
“More than 4 million repositories in Docker Hub are imageless and contain nothing except the repository files,” JFrog security researcher Andrey Polkovnichenko said in a report shared with The Hacker News.
More importantly, this file has nothing to do with the container. Instead, it is a webpage designed to lure users to a phishing or malware-hosting website.

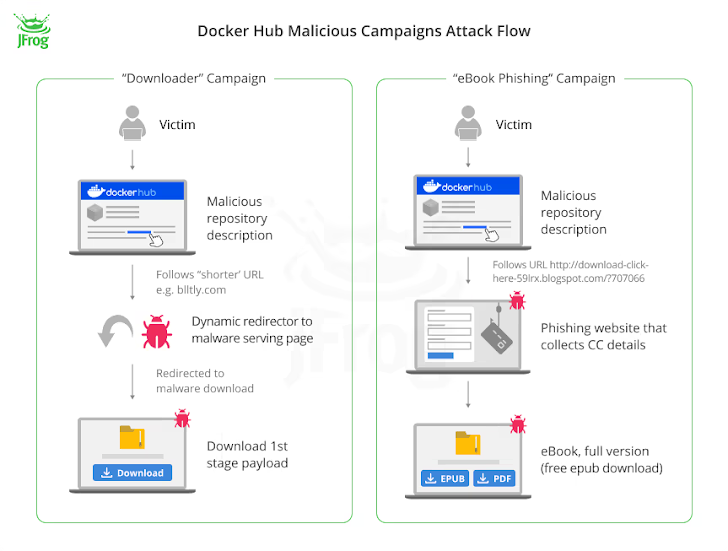
Of the 4.79 million imageless Docker Hub repositories discovered, 3.2 million of them are said to be used as landing pages to redirect unsuspecting users to fraudulent websites as part of three broad campaigns:
- Downloaders (repositories created in the first half of 2021 and September 2023) that promote purported links to pirated content or video game cheats, but either link directly to malicious sources or to legitimate sources that in turn contain Redirect to malicious payload after 500 milliseconds.
- The e-book phishing (a repository created in mid-2021) redirects users searching for e-books to a website (“rd.lesac.ru”), which in turn urges them to enter financial information to download the e-book.
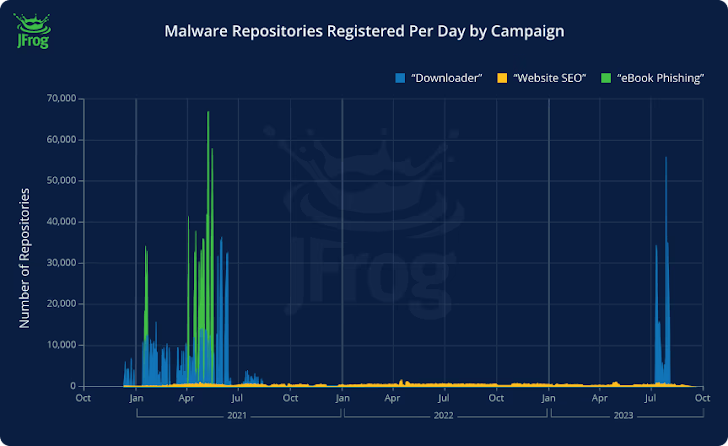
- website (thousands of repositories were created daily from April 2021 to October 2023), which in some cases contained links to an online diary hosting service called Penzu.
The payload delivered as part of the download campaign is designed to contact a command and control (C2) server and transmit system metadata, which then responds with a link to the cracked software.
On the other hand, the exact goals of the website cluster are currently unclear, and the campaign also spreads on websites with lax content moderation policies.

“The most concerning aspect of these three campaigns is that users can’t do much to protect themselves in the first place other than exercising caution,” Shachar Menashe, senior director of security research at JFrog, said in a statement shared with JFrog.
“We are essentially looking at a malware playground that, in some cases, has been three years in the making. These threat actors are very motivated and hide behind the credibility of the Docker Hub name. Lure the victim.
As the XZ Utils leak demonstrates, threat actors go to great lengths to poison well-known utilities, so developers must exercise caution when downloading packages from the open source ecosystem.
“As Murphy’s Law states, if something can be exploited by malware developers, it inevitably will be exploited, so we expect these campaigns to be found in more repositories than just It’s Docker Hub,” Menashe said.
