
The 2023/2024 Axur Threat Landscape Report provides a comprehensive analysis of the latest cyber threats. This information combines insights from the platform’s surveillance data on the surface, deep and dark webs with in-depth research and investigations conducted by our threat intelligence team.
Learn about the full scope of digital threats in the Axur Report 2023/2024.
Overview
In 2023, the cybersecurity landscape witnessed a significant increase in cyberattacks.
One notable shift is the integration of cyber risk with business risk, a concept that is becoming increasingly popular in boardrooms around the world. As the magnitude of the damage caused by cyberattacks becomes apparent, organizations are beginning to reassess their strategies.
Geopolitical factors play an important role in affecting information security. Conflicts between countries such as Russia and Ukraine have had a knock-on effect, affecting the strategies of cybercriminals. This is the year where external factors and digital threats intertwine.
Ransomware attacks, once primarily focused on encryption, have taken a new turn. Threat actors prioritize data breaches, targeting organizations that have been hit with hefty fines for data breaches. The stakes are higher than ever.

Artificial intelligence has become a powerful weapon in cyber attacks. From deepfake videos of celebrities to automated social engineering, the role of artificial intelligence in cybercrime has greatly increased.
One example is a fake video that uses celebrities to promote cryptocurrency scams
Examples include billionaire Elon Musk and Ethereum founder Vitalik Buterin.video use
Images of these executives at the event, but with the original lines replaced with
AI synthesized sounds. Changing the image just to ensure lip sync is another feature of this type of artificial intelligence.
Hacktivist groups have also left their mark, allying themselves with all sides in global conflicts. Their symbolic attacks pose risks to individuals and organizations, highlighting the need to remain vigilant in an interconnected world.
Let’s dig into the platform’s data, summarized here 7 key findings.
Key findings:
1. The number of leaked cards tripled
The report shows a disturbing escalation in cyber threats. A staggering 13.5 million credit and debit card details were leaked in 2023, triple the number from the previous year. The United States tops the list, accounting for nearly half of all detected bank card breaches. This surge reflects increased activity in deep web and darknet pipelines, where this type of data is frequently traded.
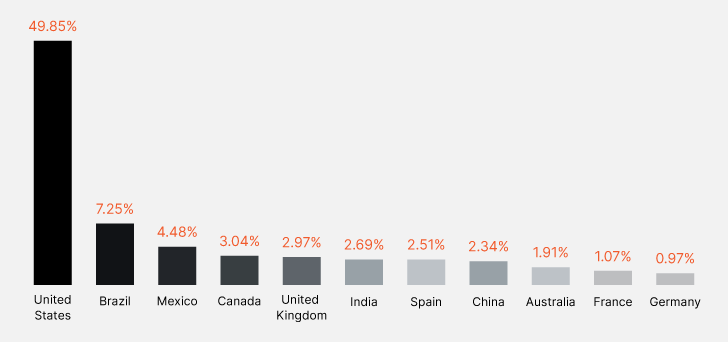 |
| Top 10 countries with the highest card exposure |
2. Focus on credential leakage and information thieves
Credential leaks, while stable at 4.2 billion, have changed as the number of placards has surged and major leaks have emerged as sources. Notably, 15% of these exposed credentials could be considered enterprise credentials, underscoring the urgency for strong enterprise cybersecurity measures.
Notably, credential-stealing malware poses a significant threat by bypassing encryption barriers and obtaining 98% of credentials in plain text. These stolen passwords are carefully recorded in log files, providing cybercriminals with insights into how to obtain them. Additionally, credential thieves can harvest authorization tokens and cookies, potentially compromising multi-factor authentication.
 |
| Sources of Credential Breaches in 2023 |
3. Panorama of brand abuse and digital fraud
Non-traditional brand impersonation such as social media profiles, apps and paid advertising resulted in 200,680 detections in 2023, a slight increase from the previous year.
 |
| Types of brand abuse in 2023 |
Explore the Threat Landscape Report for cutting-edge insights and solutions.
4. New Scams: Changing Tactics
The report proposes a series of novel strategies that deserve our attention. Notably, threat actors now have the ability to leverage popular platforms to build complete e-commerce stores in minutes.
In addition, the rise of “phishing” scams has become a focus, demonstrating the increasing sophistication of contemporary online fraud. In these scams, malicious applications disguise themselves as legitimate browsers and load cloned pages under the control of cybercriminals. This emerging trend highlights the need for increased vigilance and innovative countermeasures to effectively address these evolving threats.
5. Behind the Outage Metrics: Downtime vs. Uptime
Last year, Axur performed 330,612 takedowns (removal of a website or page from the web), with an extremely high success rate, especially against threats such as phishing (96.85%) and fake accounts (97.63%). The highlight of this process is the automated notification workflow that significantly reduces the time between incident identification and provider notification.
For example, Axur initiates phishing case notifications within 5 minutes, providing efficient processing for entities such as Shopify, Cloudflare, Namecheap, Hostinger, and GoDaddy, often within the same day. When it comes to addressing brand counterfeiting, accounts can be removed from platforms like Facebook and Instagram upon notification (usually within an average of 41 minutes and 56 minutes respectively).
 |
| Removal response times by organization and platform |
6. Deep Web and Dark Web Insights: Monitoring the Underworld
Analysis of 133 million messages and posts on the deep and dark web provides insights into the strategies and procedures of malicious agents, playing a vital role in preventing cyber threats. This surveillance extends to messaging apps like Telegram, WhatsApp and Discord, as well as deep web forums and illicit marketplaces where cybercriminals trade leaked data, compromised computer access and illicit services.
There were over 529,965 incidents across monitored deep web and dark web sources, primarily in the retail/e-commerce, financial institutions, and technology services industries.
 |
| The most attacked industries on the deep and dark web in 2023 |
Notably, 374,592 incidents were caused by text detection, while 155,373 incidents were caused by audio, video or image detection. Multimedia content analysis is becoming increasingly important as it can reveal hidden threats and enhance overall threat visibility.
7. Artificial Intelligence: A new frontier for cybercrime
Artificial intelligence (AI) tools facilitate software and content creation, but are now being used for malicious purposes. These tools allow scammers to craft more convincing narratives and interactions, thereby increasing the sophistication of their scams. Axur, on the other hand, is pioneering the use of generative artificial intelligence in cyber defense with the launch of Polaris.

Polaris: an automated threat management platform powered by artificial intelligence
At the heart of this AI-driven platform, specialized large-scale language models sift through vast pools of data to deliver customized, actionable insights directly related to an organization’s unique attack surface. This innovative approach not only streamlines the threat intelligence process but also ensures security teams focus on policy response, increased productivity and decision-making.

Polaris marks a departure from the overwhelming, fragmented nature of traditional threat management, providing a cohesive and focused view that facilitates rapid, informed action on potential threats, dramatically reducing analysis time and enhancing organizational response capabilities.

Your automated threat Intel analyst: Start your 15-day Polaris trial now
in conclusion
The Axur report illuminates the complex and evolving cyber threat landscape, with a particular emphasis on vulnerabilities and challenges facing the United States. The data presented highlights the urgent need for organizations to adapt and strengthen their cybersecurity frameworks to respond to increasingly sophisticated cyber threats.
To cope with the complexity of the current cybersecurity landscape, organizations must focus on two key strategies:
1. Comprehensive monitoring and quick response:
The essence of strong cybersecurity lies in the efficiency of extended monitoring and response mechanisms for digital assets. Organizations must ensure in-depth monitoring of their digital ecosystems, including tracking the origin of credentials, monitoring the proliferation of fake profiles and applications, and vigilant oversight of deep web and darknet activity.
This thorough monitoring must be combined with a fast, decisive response to minimize the window of exposure to potential fraud and digital risks. By promptly identifying and resolving threats, organizations can significantly mitigate the impact of cyber incidents.
2. Leverage artificial intelligence for threat intelligence and automation:
Harnessing artificial intelligence is becoming not just beneficial, but critical. With manual work no longer feasible, AI-driven technologies offer unparalleled advantages in scaling and automating the detection and elimination of cyber threats. By adopting advanced security solutions powered by artificial intelligence, organizations can enhance threat monitoring and analysis capabilities.
This not only ensures a quick and informed response to cyber incidents, but also strengthens an organization’s overall defense framework. Adopting a multi-layered security approach that combines proactive prevention and reactive strategies, as well as the analytical capabilities of artificial intelligence, ensures a more resilient defense against increasingly complex cyber threats.
Learn more about Axur
Axur is a cutting-edge external threat intelligence platform known for its end-to-end automation, top-tier removal capabilities, and scalable intelligence. Axur empowers information security teams to ensure a more secure digital experience by detecting, inspecting and containing threats at the external perimeter.
